Where is MD5 used? (Most common applications explained)
MD5 is a cryptographic hash function, that has many advantages like the speed to generate them and the almost irreversible algorithm. These have leaded the MD5 algorithm to be widely used in the past, but where is this function still used nowadays?
The most common application of the MD5 algorithm is now to check files integrity after a transfer. By generating a MD5 file before and after a file transfer, it’s possible to identify any corruption. MD5 is also still used to store passwords in some databases, even if it’s no longer safe.
In this article, I’ll introduce both applications and give you some links to learn more about each of them.
Secure your spot in the Accelerator Program, with early access to exclusive resources.
Get 1000+ classes, unlimited mentorship, and more.
Table of Contents
Your essential Linux handbook
Want to level up your Linux skills? Here is the perfect solution to become efficient on Linux. 20% off today!
Download now
Reminder about the MD5 algorithm
MD5 stands for “Message Digest algorithm 5”.
It’s a hash function that will convert any input (number, string or file from any length) to an output containing 32 hexadecimal characters.
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
For example, the MD5 hash corresponding to the string “MD5Online” is “d49019c7a78cdaac54250ac56d0eda8a”.
There is no logic in the result, and if you have only the MD5 hash, good luck to find the original value.
The main strengths of this algorithm compared to other solution is the native support on any operating system and the speed to generate a MD5 hash. It won’t slow any process, so it’s perfect to use it even with large dataset.
Using MD5 as an integrity checker
The MD5 algorithm is now mostly used to check files integrity after a transfer. With large files especially, you’ll often find a MD5 file on the download page, allowing you to check if the download is complete and valid.
In general, a MD5 file contains only one MD5 hash. This hash is the fingerprint of a bigger file, generated with the md5sum program. As you might know, the MD5 algorithm is not perfect, but it always gives the same result for a specific input. If the input doesn’t change, the output will always be the same hash.
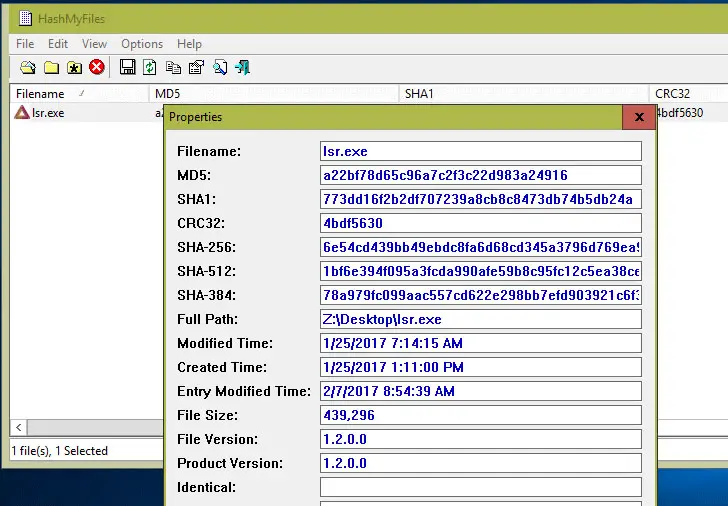
There are many tools that can be used to generate a MD5 file (link to my article on the topic). Whatever the operating system you use, you should be able to quickly find a solution, either a native way to do it (often in command line) or by installing a graphical tool to do the same thing without any required skill.
The person hosting the file (let’s say a big ISO file) will share the file and the corresponding MD5 file. After downloading the ISO file, you can generate a MD5 file on your computer and compare the result with the one provided by the host.
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
I recommend reading this other article if the process is not clear enough for you.
Using MD5 to store passwords in a database
The MD5 algorithm has been popular in the past to crypt passwords in databases. The goal was to avoid keeping them in clear text. This way they were not exposed in case of security breach or hack. Since then, using the MD5 algorithm for this is no longer recommended.
Even if the MD5 function is not reversible in the literal sense of the word, it’s becoming easier each year to break them and find the original value. With technology improvements over the years, it’s now really fast to crack any short password (time to crack a password are listed here).
Try it for free now, with advanced security features.
2900+ servers in 65 countries. It's free. Forever.
Brute force, dictionaries and rainbow table are strategies that work well against MD5 hashes. Current computers can use powerful GPU resources to get a high success rate on any MD5 hash generated by a short password or common word. That’s why this second usage is less and less frequent, even if it’s still used in some code because it’s not that easy to switch to another algorithm.
If you want an example on how bad this idea is, you can check our main website MD5Online and see by yourself how fast we can decrypt most MD5 hashes. We have almost a 90% success rate for our premium customers. And our infrastructure is not that big, there is no doubt that larger hacker organizations are much better equipped.
By the way, if you are interested in how MD5 decryption really works, I highly encourage you to take a look at my e-book “The Secrets of MD5 Decryption” here. It explains everything you need to know, going directly to the point with practical examples you can test on your computer. You don’t need any hardware to get started, just a few tips I give in this book.
Whenever you’re ready for more security, here are things you should think about:
- Break free from Gmail:
You should be able to choose what happens to your data. With Proton, only you can read your emails.
Get private email.
- Protect yourself online:
Use a high-speed Swiss VPN that safeguards your privacy. Open-source, no activity logs.
Get Proton VPN risk-free.
- Master Linux commands:
A sure method to learn (and remember) Linux commands. Useful ones only, one at a time, with clear explanations.
Download the e-book.