What is a Rainbow Table? (MD5 Decryption Strategy)
The MD5 algorithm is a one-way hash function, it’s not reversible, so there is no way to decrypt a MD5 hash “automatically”. However, current technologies allow us to use different strategies to crack MD5 hashes and find the original word. Using a rainbow table is one of them, and that’s what I’ll introduce in this article.
A rainbow table is a pre-generated file that is optimized for fast password cracking. It contains all the words like a dictionary, but also the hash equivalent. They take more disk space but are faster to use than other attack methods.
In this article, we’ll see what why it’s a good strategy, how it works and how you can generate them.
Your essential Linux handbook
Want to level up your Linux skills? Here is the perfect solution to become efficient on Linux. 20% off today!
Download now
What are rainbow tables used for?
Try it for free now, with advanced security features.
2900+ servers in 65 countries. It's free. Forever.
Rainbow tables are computed files containing hashes and their password equivalents. Using a rainbow table is a common attack used by hackers to crack passwords and find the clear text version of them from a hashed value stored in a database.
As a reminder, passwords are generally not stored in clear text in website databases. Most of the time, developers put some security layers in place to avoid any major issue if the database is stolen.
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
MD5 was one of the most common hash function used in the past to do this. Other algorithms are now being used, as MD5 is no longer safe to do this, but the idea is the same.
Hackers can use different strategies to crack password (dictionary, brute force and rainbow tables are the most common ones). In this article, we’ll focus on the rainbow table attack, but you can find explanation about the other ones on this website if you are interested too.
How does a rainbow table attack work?
A rainbow table attack uses a pre-generated file containing hashes and their plain text equivalents to crack passwords stored in a database. If there is a match between a hash in the database and one in the rainbow table, the authentication is now possible, the password has been cracked.
Tools like RainbowCrack are often used to generate and use that kind of table (see next question). The generation process is complicated, but these tools will help a lot and using the tables once generated is straightforward, in short:
- A hash is identified in the website database
- The hacker run a search command to see if the hash is present in the rainbow table
- If there is a match, the hacker can now access the user account
The bigger the rainbow table is, the more chance there is to have a match.
How to generate a rainbow table?
The easiest way to generate a rainbow table is to use a tool name RainbowCrack. It’s available on Windows and Linux and can generate tables for different hash algorithms (including MD5, SHA1 and SHA256).
To generate a table, you need to use the rtgen command. There are a few parameters required:
- The algorithm: for example MD5 is a common used algorithm in rainbow tables
- The charset: what kind of word it should generate in the file (digits, alpha-numeric in lower case, special characters, etc.).
- The words length (min and max).
- Table generation functions
- And the last parameter is to tell if you want to split the file in several small files or not
If you are interested in trying this, I explain everything in my book “The Secrets of MD5 Decryption“. I highly recommend reading it if you want to learn everything about the rainbow table strategy, but also the other listed previously (brute force and dictionary, for example).
The generation will take more or less time depending on these parameters. Once the rainbow table generated, you can use another command included in RainbowCrack (rcrack) to check if a specific hash is present in the table.
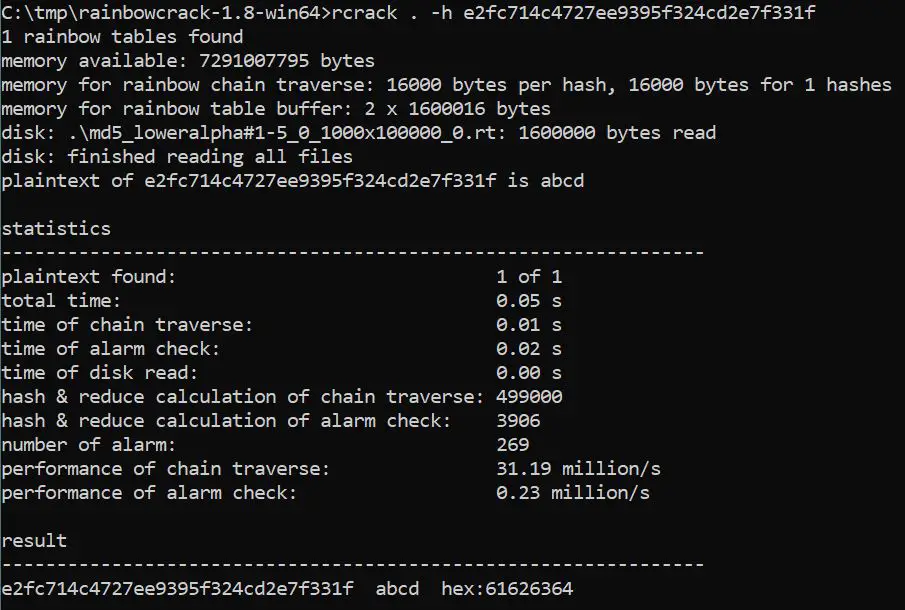
Here is an example with an MD5 hash:
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
As you can see, my basic password (“abcd”) has been found in my rainbow table, the cracking is a success in this case, and the tool stop automatically.
How big is a rainbow table?
The size of a rainbow table will be between a few megabytes and several petabytes, depending on the character set used and passwords length. For example, a 7-characters lowercase only table will take 35 MB, while an 8-characters alphanumeric table will require 1 TB.
By using the different options in RainbowCrack, it’s possible to adjust the result to make sure it fits on your hard drive or server. But basically, make sure you have large disks if you are interested in testing this at a sufficient scale. If you don’t have space for more than 7-characters passwords, a brute force attack is probably a better strategy.
Join the Complete Ethical Hacking Course Bundle and step into the world of cybersecurity.
Learn to think like a hacker and protect systems with this comprehensive course.
Tobtu.com has a tool that can help you to better estimate the file size you’ll generate with RainbowCrack. It’s not perfect, but it should give you a decent guess.
What is the best defense against rainbow table attacks?
As a general rule, the best defense against any attack, including rainbow tables, it to use long passwords, with a minimum complexity level and store them in a database by using a strong algorithm and salt. The longer the password are, the harder it will be to crack them.
Even if it helps, complexity is not really the most important factor to slow down hackers, length is. As explained in this article, there is a major difference in the attack duration for an 8-characters passwords and a 10-charaters password.
Users need to use longer passwords, even passphrase are pretty good if not too obvious, and developers must use salt to limit any major problem if a hacker get access to the database (on top of other security measures obviously).
Whenever you’re ready for more security, here are things you should think about:
- Break free from Gmail:
You should be able to choose what happens to your data. With Proton, only you can read your emails.
Get private email.
- Protect yourself online:
Use a high-speed Swiss VPN that safeguards your privacy. Open-source, no activity logs.
Get Proton VPN risk-free.
- Master Linux commands:
A sure method to learn (and remember) Linux commands. Useful ones only, one at a time, with clear explanations.
Download the e-book.