What’s The Difference Between MD5 And SHA1?
MD5 and SHA1 are often used following a random pick by the developer, but it’s not the same thing
In this post, I’ll introduce these two solutions and explain how they differ.
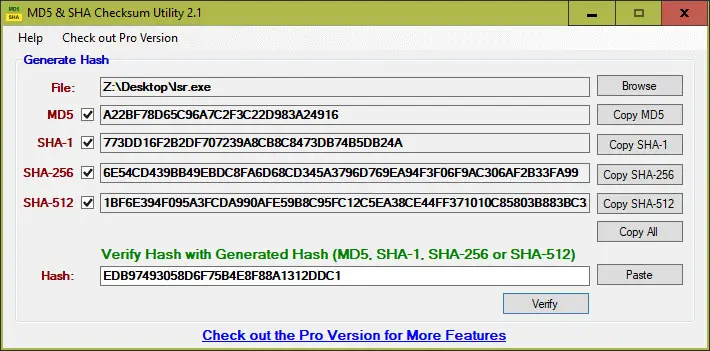
The main difference between SHA1 and MD5 is that MD5 produces a 32-character message digest, while SHA1 produces a 40-character hexadecimal. Also, the MD5 algorithm is faster than SHA1, but SHA1 is more secure than MD5.
The essential features of any hash algorithm include:
- Message digest should have a constant length.
- They shouldn’t be reversible.
- Encryption is primarily used to encrypt messages or files.
In this article, we discuss the differences between MD5 and SHA1 sequentially, by first looking at the features of each function before looking at the specific differences in terms of crack code, speed, security, supported message length, and complexity of the underlying code.
Your essential Linux handbook
Want to level up your Linux skills? Here is the perfect solution to become efficient on Linux. 20% off today!
Download now
Message Digest 5 (MD5)
Definition
The MD5 message-digest algorithm is a cryptographically broken but still widely used hash function producing a 128-bit hash value. Although MD5 was initially designed to be used as a cryptographic hash function, it has been found to suffer from extensive vulnerabilities.
Wikipedia
The MD5 algorithm has been widely used to store passwords in databases in the early years, but it shouldn’t be used anymore for this application (learn why here).
The main usage of MD5, currently, is to protect data when files are conveyed via insecure channels (HTTP, FTP, etc.).
Join the Complete Ethical Hacking Course Bundle and step into the world of cybersecurity.
Learn to think like a hacker and protect systems with this comprehensive course.
The function can also be used to provide data integrity where messages can be altered. Data packets are passed through a cryptographic hash function to create a compressed image of the message known as a digest.
Example
Let’s take, for instance, Bob received a message and digest pair from Alice.
To verify the transparency and integrity of the received data, Bob runs the cryptographic hash function on the given message to generate a new digest.
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
If the generated digest coincides with the one sent earlier by Alice, then it serves as a proof of integrity.
If the file on both end return the same result once passed through the MD5 algorithm, we can say that it’s the exact same file (some collisions are possible, but it’s very unlikely with file integrity).
Rules
From a biometric perspective, the message and digest pair is an equivalent of a physical document and a fingerprint to unlock it.
The only difference is that digest and message can be sent separately, unlike a physical document and an attached fingerprint.
Simply put:
- The digest should not be tampered with during transit.
- The cryptographic function is ideally infeasible to invert as it is a one-way function.
Message digest 5 function takes in data of any length and then generates fingerprint, hash or digest of a fixed length that is used as a check for integrity. - As an integrity checker, the message digest is encrypted with the sender’s private key to provide authenticity of the message being sent.
This generated digest is referred to as a digital key and can only be decrypted by the receiver who has the sender’s public key. This way, the receiver can verify the sender and as well authenticate the integrity of the received message.
To illustrate how this function works. You can imagine how MD5 is used to check data integrity by dividing a message into blocks of 512 bits to create a digest of 32 hexadecimal digits (128-bit digest).
Safety
MD5 however, is no longer preferred for reliable use, as researchers have exposed how the system can be bypassed by generating collisions on commercial computers.
I have several articles on this topic on the website, so I’ll let you check them if you need further details:
- Can Hashed Passwords Be Decrypted? (Not as safe as you think)
- Where is MD5 used? (Most common applications explained)
- Is MD5 Reversible? (Truth, Myths and Solutions)
Video
If you need a visual support to really understand how it works, here is an interesting video on the topic:
SHA1
Definition
In cryptography, SHA-1 (Secure Hash Algorithm 1) is a cryptographically broken but still widely used hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest – typically rendered as 40 hexadecimal digits.
Wikipedia
SHA1 is part of cryptographic functions created to keep data safe.
Generally, they are referred to as a secure hash algorithm, and they work by transforming messages using a hash function.
These functions are algorithms made up of compression functions, bitwise operations, and modular additions.
These algorithms are designed to be a one-way function that transforms the input data into a fixed size that is different from the first one.
Secure hash algorithm family are SHA- 1, SHA – 2, and SHA- 3, all of which were developed and enhanced as per hacker activities. For instance, SHA-0, the first generation of secure hash algorithms, is now obsolete due to the widely exposed vulnerabilities.
How does it work?
As for this article, we will focus on SHA-1 (The Secure Hash Algorithm 1), a cryptographic computer security algorithm developed by the US National Security Agency in 1995. It was preceded by the SHA-0 algorithm, created in 1993.
SHA-1 is part of the Digital Signature Standard (DSS) and (or) Digital Signature Algorithm.
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
SHA-1 generates a 160-bit hash value or message digest from the input data that requires encryption. The generated data resembles the hash value of the MD5 algorithm. The whole process takes 80 rounds of cryptographic operations to secure data packets.
Below are some protocols used in SHA-1:
- Pretty Good privacy
- Transport Layer Security
- Internet Protocol Security
- Secure Shell
- Multipurpose Internet Mail Extensions
- Secure Sockets Layer
In Practice
SHA-1 is normally used where there is a high need for data integrity or in hostile environments. The technique is also used to identify checksum errors and data corruption and as well as index functions.
Differences between MD5 and SHA-1
SHA1 and MD5 are both hashing algorithms, with MD5 being the most efficient in terms of speed.
However, SHA1 is the most secure algorithm compared to MD5.
Try it for free now, with advanced security features.
2900+ servers in 65 countries. It's free. Forever.
The basis of both hashing algorithms is their ability to generate an encrypted digest or hash from a message received.
Some essential elements for both functions include:
- There can never be two similar hashes or digest as data sets are unique.
- The size of the message being conveyed does not influence the length of the digest or hash generated.
- Once executed, these functions cannot be undone or reversed.
Hash algorithms are primarily designed to verify files instead of encrypting the message sent.
| MD5 | SHA1 |
| MD5 is an acronym for Message Digest | On the other hand, SHA1 refers to the Secure Hash Algorithm. |
| Compared to SHA1, MD5 is still fast and more reliable in terms of speed. | Likewise, the speed of SHA1 is relatively slow in comparison to that of MD5. |
| The message digest is of 168 bits in length | While in SHA1, there can be up to 160 bits length of message hash. |
| MD5 is simple when compared to SHA1 | SHA1 is more complex than MD5 |
| An aggressor would require 2^128 operations to make the first message using the MD5 algorithmic program. | While in SHA1, an aggressor will require 2^160 operations hence quite challenging to find out. |
| In MD5 an assailant would need to perfume 2^64 operations to find out if any two messages share the same message digest. | On the opposite side, an assailant would need 2^80 operations in SHA1, to find out the two messages with the same hash or digest. |
| MD5 provides poor or indigent security | SHA1 provides tolerable or balanced security. |
Message Digest length for MD5 and SHA1
According to the Federal Information Processing Standard, there are four secure hash algorithms, namely SHA-1, SHA-256, SHA-384, and SHA-512.
All the four functions are iterative and one-way functions that can compress messages with lengths of between 264 to 2128 to produce a message digest of about 160 – to 512- bit.
MD5 on the other hand produces a message digest or “fingerprint” equivalent of 128- a bit from an input message of an arbitrary length.
Security
MD5 is expressed as a 32-digit hexadecimal number that is cryptographically broken and can have collisions.
Despite its popularity as one of the most commonly used hash functions, it is not the most preferred security-based service for systems that rely on collision resistance.
On the other hand, SHA is believed to be more secure than MD5.
It takes a large number of bits as input and generates a shorter and more secure output of fixed size.
Currently, there are better versions of SHA1 where most vulnerabilities have been eliminated such as SHA-256, SHA-384, SHA-512.
The suffix indicates the level of strength of the message digest.
Conclusion
The main and most significant difference between MD5 and SHA1 is that MD5 was the first one to be developed and had several vulnerabilities that could be exploited by intruders to create collisions for message digest or hash.
SHA1 was therefore an enhancement of MD5 in terms of functionality and as well security-wise. Vulnerabilities in the first version of SHA1 has since then been eliminated through subsequent releases, that is, SHA 256 and SHA 512.
Whenever you’re ready for more security, here are things you should think about:
- Break free from Gmail:
You should be able to choose what happens to your data. With Proton, only you can read your emails.
Get private email.
- Protect yourself online:
Use a high-speed Swiss VPN that safeguards your privacy. Open-source, no activity logs.
Get Proton VPN risk-free.
- Master Linux commands:
A sure method to learn (and remember) Linux commands. Useful ones only, one at a time, with clear explanations.
Download the e-book.